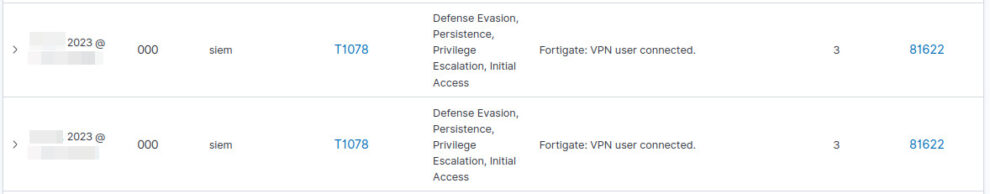
TL;DR Integrating Fortinet VPN activity with Wazuh SIEM in order to enhance it with geolocation capabilities. The goal was to improve network visibility and strengthen the investigation process for VPN-related events.
We aim to enhance visibility on network activities, particularly regarding VPN access. We need to gain insight not only on failed VPN login but also into successful ones in order to detect and analyze anomalies such as stolen VPN access.
To achieve this, we have integrated Wazuh SIEM with Fortigate to collect event data via syslog. By default, FortiOS sets the syslog level to “warning.” In order to capture successful VPN login events and expand our logging capabilities, we need to adjust the syslog severity to “information” using the command-line interface (CLI).
# config log syslogd filter # set severity information # show full-configuration

At this stage, also successful VPN logins will be reported via syslog. To verify this, you can check via tcpdump on your SIEM platform in conjunction with grep.
# tcpdump -A -nnn udp and host [FORTIGATE IP] | grep tunnel-up [...] date=2023-XX-XX time=11:XX:00 devname="XXX" devid="XXXXXXXX" eventtime=XXXXXXXXXXXXXXX tz="+0200" logid="XXXXXXX" type="event" subtype="vpn" level="information" vd="root" logdesc="SSL VPN tunnel up" action="tunnel-up" tunneltype="ssl-web" tunnelid=XXXXXXX remip=XXX.XXX.229.187 user="XXXXXXXX" group="VPN" dst_host="N/A" reason="login successfully" msg="SSL tunnel established" [...]
So, now we have both failed and successful VPN logins (as well as VPN logout events). However, there is an issue with FortiOS, as it puts the public IP address of users in the “remip” field. While Wazuh decoders can successfully parse this field, it does not provide geolocation information, which is crucial for investigations, such as detecting remote and unauthorized logins.
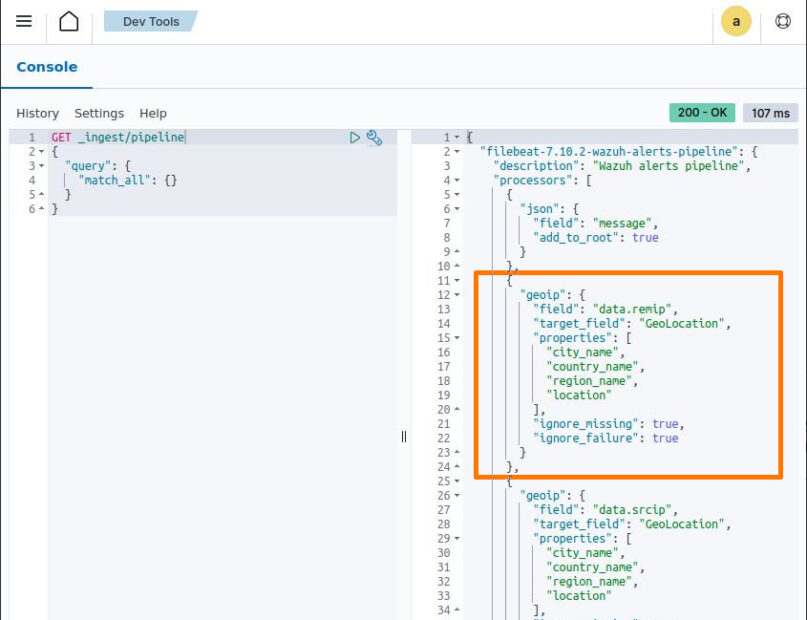
To include geolocation information in this field, we need to modify the FileBeat configuration on the Wazuh system by adding the following:
{
"geoip": {
"field": "data.remip",
"target_field": "GeoLocation",
"properties": ["city_name", "country_name", "region_name", "location"],
"ignore_missing": true,
"ignore_failure": true
}
},
to /usr/share/filebeat/module/wazuh/alerts/ingest/pipeline.json and /usr/share/filebeat/module/wazuh/archives/ingest/pipeline.json.
After, we need to tell FileBeat to take care of this, running:
# filebeat setup --pipelines
We can check whether the pipeline has been updated or not by running the GET _ingest/pipeline query using the Wazuh Dashboard Dev Tool.
Great! With the modifications made to the FileBeat configuration on the Wazuh system, the Wazuh events should now include VPN events with geolocation information. This will greatly enhance the visibility and investigation capabilities for detecting and analyzing VPN-related activities.
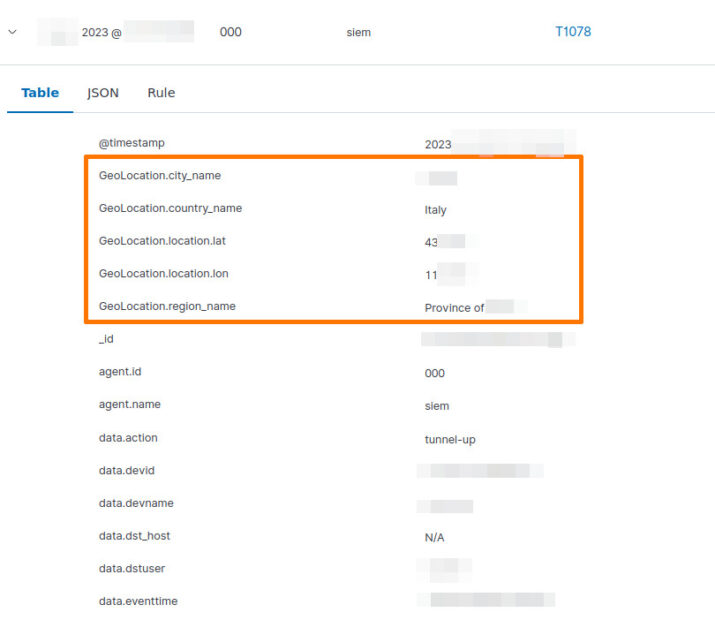
Please ensure that the changes have been applied correctly and monitor the Wazuh events to verify the presence of geolocation information for VPN events. If everything is functioning as expected, you should now have a more comprehensive understanding of VPN access and be better equipped to identify any suspicious or unauthorized activities.
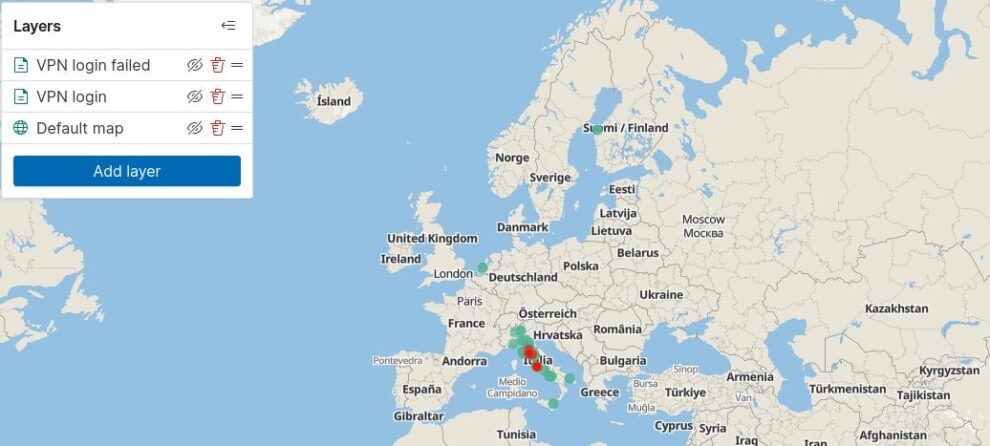
Playing with visualization on OpenSearch dashboard, it’s easy to have a world map with successfully and failed login via VPN.
Good luck with your network visibility and VPN monitoring efforts!

2 comments
you should commit this to GitHub https://github.com/wazuh/wazuh/tree/3dd0177b31c207b5c25a9a1b4cab0229be3b03ca/extensions/filebeat/7.x/wazuh-module .
Thanks for the guide but do you know which site/database Wazuh uses for Geolocation? It shows a lot of wrong countries in the Europe meanwhile the correct one is from USA.