Wazuh is a poweful open source SIEM solution. To be honest, is something more than a SIEM: integrating with its OSSEC agents, it became a flexible XDR solution to protect your digital assets in real-time.
One of the most challenging steps in configuring a SIEM is setting up the log decoders and rules. While pre-built decoders are available for most common log formats, there may be times when you need to add a new decoder to allow Wazuh to correctly parse messages.
As you may have noticed, Freeradius logs are not yet included by default in Wazuh’s decoder collection. Therefore, before you can collect and correlate events from the Freeradius RADIUS server, you will need to create a new decoder.
But before doing that, don’t forget to install wazuh-agent in Freeradius server and make the necessary changes to the ‘/var/ossec/etc/ossec.conf’ to monitor ‘radius.log‘:
<localfile>
<log_format>syslog</log_format>
<location>/var/log/freeradius/radius.log</location>
</localfile>Then restart wazuh-agent:
systemctl restart wazuh-agentAfter completing the previous steps, return to the Wazuh SIEM console and begin adding the Freeradius decoder and rules.
Next, navigate to the ‘/var/ossec/etc/decoders‘ directory, which houses custom decoder definitions. Create a new file called ‘freeradius_decoder.xml‘ (or choose a name of your preference) and include the following content within the file::
<!--
FreeRadius Wazuh decoder
based on Asier Gonzalez Diaz work (https://www.linkedin.com/pulse/integrating-freeradius-logs-our-favorite-siem-wazuh-gonzalez-diaz-grggf/)
reviewed by Michele <o-zone@zerozone.it> Pinassi
-->
<decoder name="freeradius_auth">
<prematch>Auth: \((\d+)\)\s+Login OK</prematch>
</decoder>
<decoder name="freeradius_auth_fail">
<prematch>Auth: \((\d+)\)\s+Login incorrect</prematch>
</decoder>
<decoder name="FREERADIUS_OK">
<parent>freeradius_auth</parent>
<regex>Login OK: [(\S+)] \(from client (\S+) port \d+ cli (\w+-\w+-\w+-\w+-\w+-\w+)</regex>
<order>username, authenticator, mac-address</order>
</decoder>
<decoder name="FREERADIUS_FAIL">
<parent>freeradius_auth_fail</parent>
<regex>Login incorrect \((\S+): \.*: [(\S+)/\.* \(from client (\S+) port \d+ cli (\w+-\w+-\w+-\w+-\w+-\w+)</regex>
<order>eap_method, username, authenticator, mac-address</order>
</decoder>Decoders are build with a PCRE2 regular expression syntax. You can build it using tools like regex101.com and test with wazuh-regex utility before using in production.
After creating the Freeradius decoder, the next step is to add rules that will enable the correct usage of events.
To do this, move to the ‘/var/ossec/etc/rules/‘ directory. Once inside the directory, create a new file named ‘freeradius_rules.xml‘ and include the following content within the file:
<!--
FreeRadius Wazuh rules
Source: https://www.linkedin.com/pulse/integrating-freeradius-logs-our-favorite-siem-wazuh-gonzalez-diaz-grggf/
-->
<group name="freeradius_auth_group">
<rule id="100800" level="0" noalert="1">
<decoded_as>freeradius_auth</decoded_as>
<description>Freeradius messages grouped.</description>
</rule>
<rule id="100801" level="0" noalert="1">
<decoded_as>freeradius_auth_fail</decoded_as>
<description>Freeradius fail message grouped.</description>
</rule>
<rule id="100811" level="3">
<if_sid>100800</if_sid>
<match>Login OK</match>
<description>Freeradius correct login.</description>
</rule>
<rule id="100812" level="8">
<if_sid>100801</if_sid>
<match>Login incorrect</match>
<description>Freeradius incorrect login.</description>
</rule>
</group>then restart wazuh-manager:
systemctl restart wazuh-managerand test it with:
/var/ossec/bin/wazuh-logtestwith a line from radius.log. You can test with those two samples:
Auth: (169017) Login OK: [anonymous@test.it] (from client radiustest port 1 cli FF-11-22-33-44-55)
Auth: (169027) Login incorrect (eap: Failed continuing EAP TTLS (21) session. EAP sub-module failed): [anonymous@test.it/<via Auth-Type = eap>] (from client radiustest port 1 cli FF-11-22-33-44-55)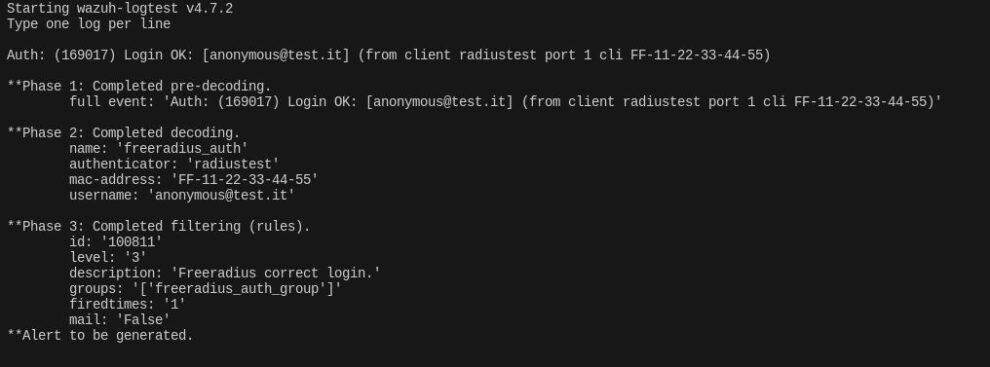
note decoded fields (Phase 2): authenticator, mac-address and username. These fields will be populated in securty alert entries and can be utilized for visualization, alerting and other purposes.
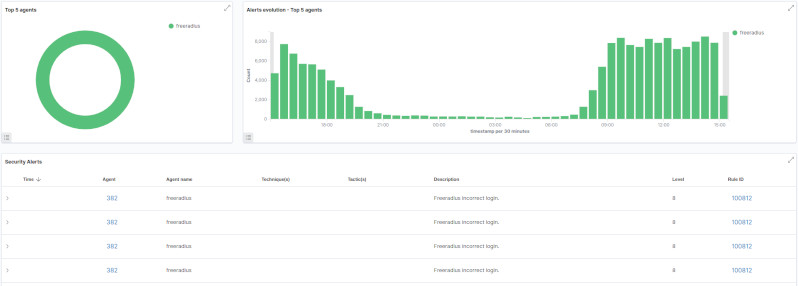
So, if all were correct, in Security events page the incoming events from Freeradius should appear (here’s my dashboard):
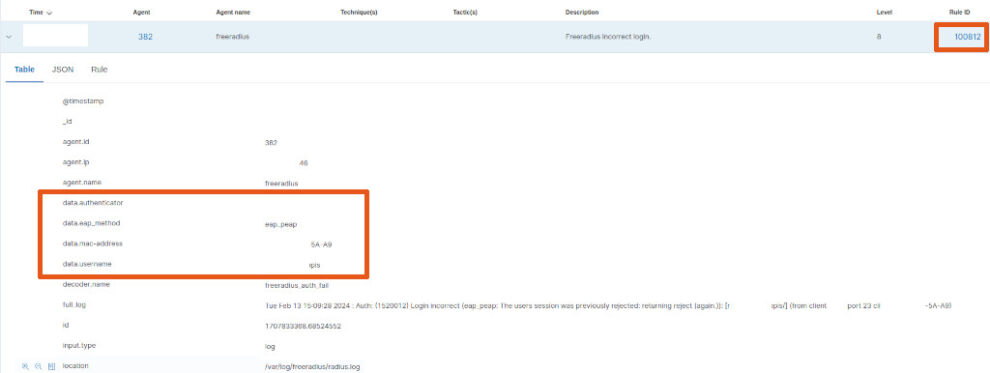
and for each alert, you’ll have the decoded data:
Hope this article could be useful and feel free to ask, leaving a comment below.
